@g you know I just tried it and TL;DR my account is locked, the restore process doesn't work, can't get the chat AI to restore it either, have to wait for office hours to get a human to intervene xD
Setting up the passkey
I was using my Yubikey and it went without any issues. The onboarding process was smooth-ish.
Then, as expected was instructed to login again and I got disonnected.
Re-login process
The "use a passkey" prompt was covering my 1Password prompt in the username field, but ok. I don't imagine non technical people loving this...
Anyway, the passkey was accepted at this point but I still had to solve a puzzle to prove that I a human (isn't that the entire point with FIDO2? Especially with a physical key that also has a mandatory PIN)
BUT in spite of all this, the passkey was not actually enough to let me in. There was a full page message telling me to please scan the QR Code with my passkey device (lol that's a Yubikey) or get a link via email and, again, scan something with the same device (lol again)
Account recovery
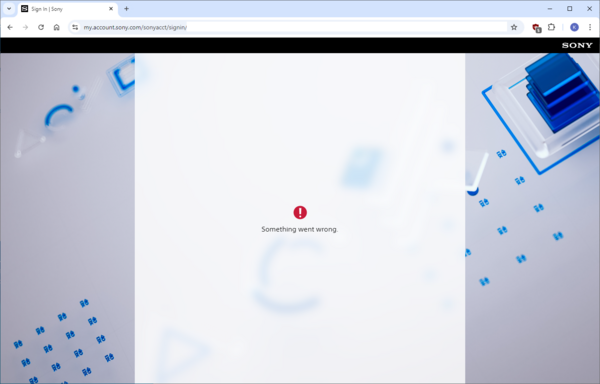
No go.
Actually, it went smoothly: got the email that my passkey was disabled, got the email that my password was changed.
But I can't get in.
Sad.
LemonLDAP::NG 2.21 is out!
This new release includes improvements on OpenID Connect and CAS protocols, Loki logger, public notifications and much more.
Read our release notes: https://projects.ow2.org/view/lemonldap-ng/lemonldap-ng-2-21-0-is-out/